2 months ago
2 months ago
🕵️♂️ MetaDetective
Unleash Metadata Intelligence with MetaDetective.
Bridging the chasm in metadata extraction and analysis.
Link : https://github.com/franckf...
Unleash Metadata Intelligence with MetaDetective.
Bridging the chasm in metadata extraction and analysis.
Link : https://github.com/franckf...
2 months ago
2 months ago
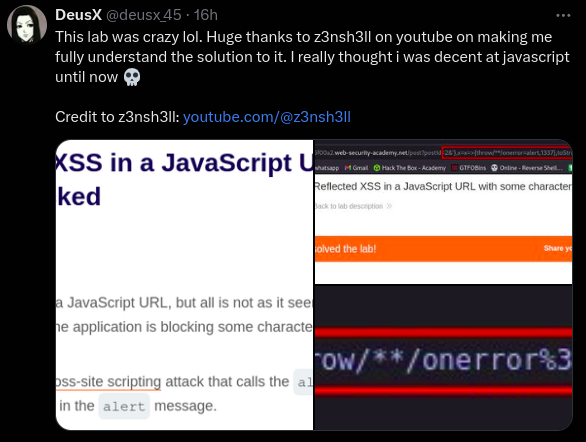
Exploring Security Vulnerabilities in HTB's Chemistry CTF
In this Capture the Flag (CTF) challenge from Hack The Box, we tackled the “Chemistry” box, where reconnaissance played a pivotal role. Here’s an overview of the methodology used to exploit the vulnerabilities.
Recon and Initial Findings
Using Nmap, we discovered open ports—22 (SSH) and 5000, a Python-based web server using Werkzeug. Port 5000 hosted a “Chemistry CIF Analyzer” web application, enabling CIF (Crystallographic Information File) uploads for structure analysis. CIF files store crystal structure data, and handling them securely is crucial.
Upload Testing and CIF Analysis
We tested the upload functionality by uploading a sample CIF file, which returned a 404 error but hinted at a server path /structure. This behavior suggested a possible CIF parsing vulnerability using the pymatgen library. Outdated versions of Werkzeug and Python increased the likelihood of security flaws.
Exploitation via Deserialization and CIF Structure
Using a deserialization exploit in pymatgen, we crafted a malicious CIF file, embedding a reverse shell payload. This approach leveraged the server’s vulnerable parsing mechanisms. By executing the payload, we gained access to a low-privilege shell.
Hash Cracking and Privilege Escalation
Further exploration revealed an MD5-hashed database containing user credentials. Using hash-cracking tools, we obtained plaintext passwords, granting SSH access to the “rosa” user. From there, tunneling enabled us to exploit another service running on port 8080, where aiohttp, an outdated Python asynchronous server framework, revealed a directory traversal vulnerability (CVE-2024-23334). This allowed us to escalate privileges and access sensitive files.
Conclusion
This CTF highlighted critical security aspects: outdated dependencies, deserialization flaws, and improper file handling can expose applications to severe vulnerabilities. Continuous updates, secure file parsing practices, and dependency management are essential in safeguarding applications from these threats.
#hackthebox
In this Capture the Flag (CTF) challenge from Hack The Box, we tackled the “Chemistry” box, where reconnaissance played a pivotal role. Here’s an overview of the methodology used to exploit the vulnerabilities.
Recon and Initial Findings
Using Nmap, we discovered open ports—22 (SSH) and 5000, a Python-based web server using Werkzeug. Port 5000 hosted a “Chemistry CIF Analyzer” web application, enabling CIF (Crystallographic Information File) uploads for structure analysis. CIF files store crystal structure data, and handling them securely is crucial.
Upload Testing and CIF Analysis
We tested the upload functionality by uploading a sample CIF file, which returned a 404 error but hinted at a server path /structure. This behavior suggested a possible CIF parsing vulnerability using the pymatgen library. Outdated versions of Werkzeug and Python increased the likelihood of security flaws.
Exploitation via Deserialization and CIF Structure
Using a deserialization exploit in pymatgen, we crafted a malicious CIF file, embedding a reverse shell payload. This approach leveraged the server’s vulnerable parsing mechanisms. By executing the payload, we gained access to a low-privilege shell.
Hash Cracking and Privilege Escalation
Further exploration revealed an MD5-hashed database containing user credentials. Using hash-cracking tools, we obtained plaintext passwords, granting SSH access to the “rosa” user. From there, tunneling enabled us to exploit another service running on port 8080, where aiohttp, an outdated Python asynchronous server framework, revealed a directory traversal vulnerability (CVE-2024-23334). This allowed us to escalate privileges and access sensitive files.
Conclusion
This CTF highlighted critical security aspects: outdated dependencies, deserialization flaws, and improper file handling can expose applications to severe vulnerabilities. Continuous updates, secure file parsing practices, and dependency management are essential in safeguarding applications from these threats.
#hackthebox
2 months ago
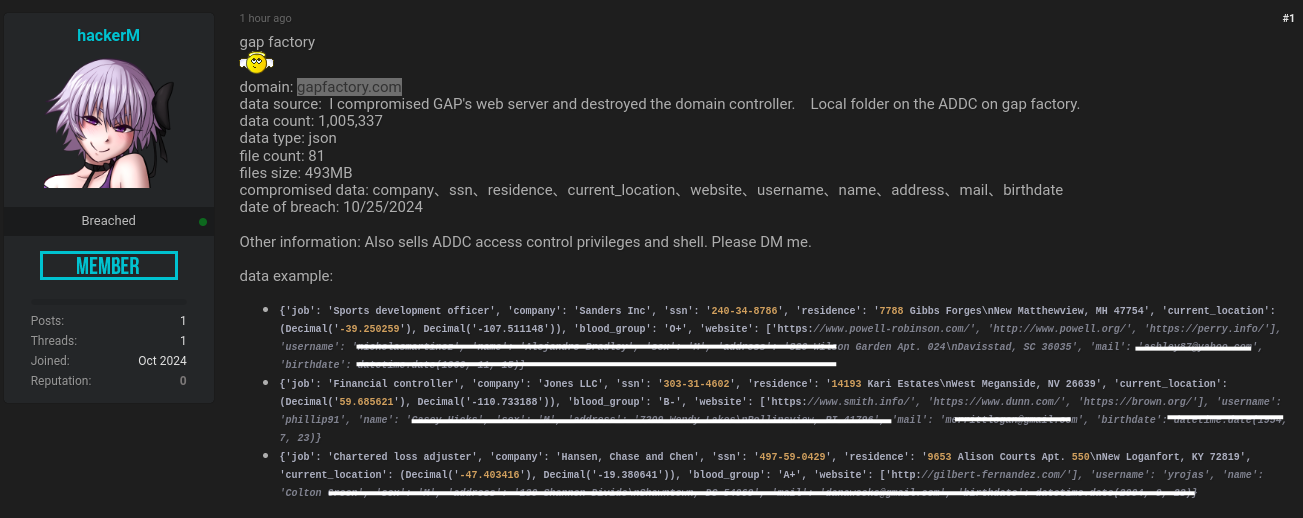
🚨 Possible Gap Factory Data Breach 🚨
Reports indicate that Gap Factory may have experienced a serious data breach, potentially exposing personal information, including SSNs, addresses, emails, and more. Hackers reportedly accessed the company’s servers and compromised sensitive data.
If this affects you, it might be a good time to monitor your accounts and be cautious of any unusual activity or phishing attempts. Stay safe online, everyone!
Reports indicate that Gap Factory may have experienced a serious data breach, potentially exposing personal information, including SSNs, addresses, emails, and more. Hackers reportedly accessed the company’s servers and compromised sensitive data.
If this affects you, it might be a good time to monitor your accounts and be cautious of any unusual activity or phishing attempts. Stay safe online, everyone!
Sponsored by
Zed Underson
2 months ago